- What Is A Decryption Key
- Rsa Decryption Key Calculator
- Rsa Decryption Key Calculator 2020
- Dvd Decryption Key
What Is A Decryption Key
CryptographyA Basic Public Key Example. The elementary working of Public Key Cryptography is best explained with an example. Rsa Decryption Key Calculator' />The working below covers the making of simple keys and the encryption and decryption of a sample of plain text. By necessity, the example is greatly simplified. Basic Public Key SummaryeditPublic key encryption is used for internet secure links, such as when a browser opens a bank site or a site used with credit cards. Such addresses are prefixed by https as opposed to just http. RSA Open. SSL is such an encryption system. An example of this secure site marking can be seen on the address of this page this Wikibooks page when the user is logged in shows the https prefix or some alternative browser specific marking that indicates that it is considered secure. Each site has an encryption key and a decryption key of its own, termed the public and private keys respectively. Key generation algorithm A practical key generation algorithm Encryption Decryption Digital signing Signature verification Notes on practical application. Where can i find some documentation on the format of an RSA public key An RSA public key formatted by OpenSSH sshrsa AAAAB3NzaC1yc2EAAAABJQAAAQB. These are essentially very large numbers. These keys are always different, giving rise to the term asymmetrical encryption. In fact whenever we say key we mean a pair of numbers comprising the key a key number to use in the raising of powers and another number that is the modulus of the arithmetic to be used for the work. Applies to. Windows Server 2003 SP1, Windows Server 2003 R2, Windows XP SP2, Windows Server 2008, Windows Vista. Credential roaming does not apply to Windows RT devices. Users of Synology NAS systems are being targeted by ransomware that is demanding payment in exchange for the encryption keys to their files. Heres how they can. The Encrypting File System EFS on Microsoft Windows is a feature introduced in version 3. NTFS that provides filesystemlevel encryption. The technology enables. For those unfamiliar with modular arithmetic, refer to the Wikibooks page High School Mathematics ExtensionsPrimesModular Arithmetic for a good, yet simple description. Figure 1 Bob knows Alices public key and uses it to encrypt the message. Alice uses her private key to decrypt the message. Public keys are openly available for anybody to see, but private keys are not. The receiving site makes his public key available to the message sender, or by his making use of public directories. For each message transmission the sender uses this key to make the code. In this way only the private key of the recipient will decrypt it. A worked example has been provided in the text below, and the basic process can be seen in Figure 1. Can T Find Downloaded File On S3 Samsung more. In fact, the two keys used for public key encryption form a reversible function. You could encrypt with the private key and decrypt with the public key if the system designers had otherwise intended it. Of course, for less public use the public keys could just as easily be treated as secret also. This reversible nature of the key pair is useful in testing digital certificates, where the issuer encrypts a certificate with his private key so that the recipient can then use his freely available public key to test its authenticity. The numbers used are made deliberately very large, and this makes the task of obtaining the private key from the public key too difficult for a hacker. It involves the factorization of very large numbers, and is very time consuming. Such systems, although imperfect, are nonetheless useful provided that the time to break them far exceeds the period for which the data is of any interest. The estimated time to break some such codes is many thousands of years. Signed digital certificates help certify the identity of user sites and to deliver public keys. Browsers take steps to confirm their validity. The main advantage of the public key system is that there is a low administrative burden. Everything needed to send a message to a site is available in a public directory or is sent openly as a part of setting up the link. The main disadvantage of public key cryptography is that it is too slow for modern internet use. Because of this, the internet most often uses symmetric encryption for the main task a different method that uses a common key for both encryption and decryption it simply uses public key methods to conceal the symmetric keys while they are being sent to the far end. There are several methods that hackers use to break coding. The brute force cracking of a key refers to trying every possible combination of private key while testing it against the relevant cyphertext. Such testing is time consuming, because a dictionary check or human intervention is needed at each iteration to decide whether or not plain language has emerged. Also, the numbers are very large, so this method is rarely of much interest. A mathematical attack refers to the finding of the two prime numbers, the product of which makes the modulus of the publicly available key. If these can be found then it simplifies the finding of the private key more later this method has the advantage that computers can be left to the task without much intervention. At the time of writing 2. Lenstra et al, on 1. December 2. 00. 9, when an RSA 7. General Number Field Sieve GNFS. The process required two years of collaboration and many hundreds of computing machines. Today most encryption keys in use are much bigger than the one that was broken, and a 1. SSL certificate is still considered fairly safe against a mathematical attack. Note that the difficulty of breaking such a key increases exponentially with the key length. The history of successful intrusions has not involved code breaking however, but the hacking of the servers for their data and private keys. Other exploits have relied on the security omissions of individuals, or defective programming. For example, a recent SSL exploit, 2. The intention in SSL is to allow some text from the recipients server to be returned as proof of message receipt and successful decryption. For this purpose the sender can specify the length of text to return, usually a header, and in any case less than 6. Kbits in length. The core of the flaw was that if a very short message was sent but the sender asked for a larger block to be returned than was sent, the faulty program would oblige, so returning data that included other secure material from memory. Repeating this process every few seconds allowed a hacker to accumulate a large data block. The matter is stated to have been since corrected, but is said to have been available to any who knew of it for a period of about four years. Making Site Bs PUBLIC KeyeditA public key is available to all, and is used to encrypt messages that are being sent to the keys owner. Each sites computer produces two very large prime numbers, and since they are the basis of all that follows, these numbers are never revealed to any other. Prime numbers are those that have no factors other than themselves or unity. These two numbers are multiplied together to produce the modulus used in all of that sites calculations. The main public key is also derived from these primes, and determines the exponent to which the plain language numbers will be raised. This public key is available in directories and from certificate authorities, so when the SENDER wants to encrypt a message by public key cryptography he can easily use the recipients public key and modulus to do it. Each sites public key set can be made to be almost certainly different from every other. Anti Deep Ze Windows 7 more. To illustrate the point for an intending recipient, let us make a simple example with the large prime numbers replaced with very small ones. Say the two secretly held prime numbers are. Then the modulus of the arithmetic that will be used is given by their product. The encryption key can be found as follows First, using the two prime numbers, calculate the function. Select ANY number that is relatively prime to fn and less than it. Two numbers are said to be relatively prime when they share no common factors other than one. This term is also referred to as mutually prime, or coprime. The possible choices become. Say we select the public encrypt exponent 7.
- Usage Guide - RSA Encryption and Decryption Online. In the first section of this tool, you can generate public or private keys. To do so, select the RSA key size among 515, 1024, 2048 and 4096 bit click on the button. This will generate the keys for you. For encryption and decryption, enter the plain text and supply the key.
- Key Bits: 512 1024 2048 736 768 896 1280 1536 1984. Padding: NoPadding PKCS1 PKCS1OAEP (SHA1) Private Key Mode.
- Dec 04, 2015 RSA is a cryptosystem and used in secure data transmission. It is based on the difficulty of factoring the product of two large prime numbers. If we already have calculated the private 'd' and the public key 'e' and a public modulus 'n', we can jump forward to encrypting and decrypting messages (if you haven't calculated.
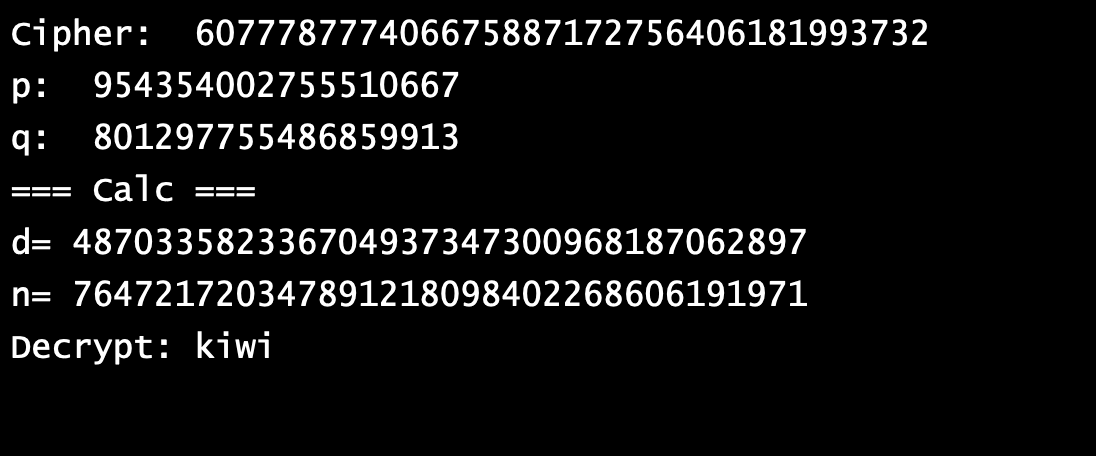
A simple app to calculate the public key, private key and encrypt decrypt message using the RSA algorithm. Find two random prime number (more than 100 better) Step 2. Choose the value of 1 mod phi. Choose the value of e and d, e (public exponential) and d (private exponential). This service allows you to create an RSA key pair consisting of an RSA public key and an RSA private key. The RSA public key is used to encrypt the plaintext into a ciphertext and consists of the modulus n and the public exponent e. Anyone is allowed to see the RSA public key. To decrypt the ciphertext, this tool creates two private keys which.
Nov. 15 Public key encryption, symmetric key encryption Examples of ElGamal cryptosystem Paper rough draft Nov. 22 Thanksgiving! Previously I was the security lead for Diem (Libra) at Facebook, and a security consultant for the Cryptography Services of NCC Group.This is my blog about cryptography and security and other related topics that I find interesting. RSA Calculator JL Popyack, October 1997 This guide is intended to help with understanding the workings of the RSA Public Key Encryption/Decryption scheme. either prove its security or show a concrete attack). Let two primes be p = 7 and q = 13. Bob (and Eve) can encrypt a message with her public key, but only the private key (which Alice has) can decrypt the message. 4 Compute y = gx mod p. P A = (p,g,y) is Alice’s RSA public key. It … • Alice generates a, 0< a < p-1, and computes ga mod p = A. ElGamal cryptosystem can be defined as the cryptography algorithm that uses the public and private key concepts to secure communication between two systems. Public Key Protocol Key-management is the main problem with symmetric algorithms – Bob and Alice have to somehow agree on a key to use. The signing protocol for an ElGamal signature is as follows. The most commonly used types of asymmetric encryption are ElGamal, RSA, DSA, and PKCS. LUC: A public key cryptosystem designed by P.J. The algorithm is based on Elliptic Curve Cryptography, a method of doing public-key cryptography based on the algebra structure of elliptic curves over finite fields. Bob also selects his secret key X between 1 and p-1. Easy to prepare ideas for desserts, pastas, grains, vegetarian and fish are updated several times a week. Its strength lies in the difficulty of calculating discrete logarithms (DLP Problem). ElGamal is a public-key cryptosystem developed by Taher Elgamal in 1985. She then chooses a secret integer z and calculates β ≡ α z (mod p). ElGamal Encryption. LetGbe the groupZ∗p={1,2,...,p−1}under multiplication modulop. 0x31 0x32 0x33 0x34 in hexmode is equivalent to 1234in string mode. Key generation [edit | edit source] The key generator works as follows: Alice generates an efficient description of a multiplicative cyclic group of order with generator. ElGamal Encryption See RSA Calculator for help in selecting appropriate values of N, e, and d. JL Popyack, December 2002. Friends, Here is the simplest ElGamal Cryptosystem implementation in SageMath. Julian Ceipek, Mar 10, 2014. The first party, Alice, generates a key pair as follows: Generate an efficient description of a cyclic group of order with generator. d. In the ElGamal public key encryption system, is it safe to fix the prime modulus p so that all users in the world use the same p? (e.g. It also explores current U.S. federal cryptographic standards, such as the AES, and explains how to authenticate messages via … The ElGamal Public Key Encryption Algorithm The ElGamal Algorithm provides an alternative to the RSA for public key encryption. MQV Key Agreement The original Diffie-Hellman method is still susceptible to a man-in-the-middle attack. This leads to the possibility of re-calculating the used private key see. (Photo courtesy of Dr. Taher Elgamal) For both RSA and ElGamal (and other systems) it is useful to know about the congruence concept. 28 RSA key generation steps 1. choose 2 primes call them p, q ... Encrypting with public key {e,n } ( c = m e mod n ) 1. choose a cleartext message call it m – in the form of a number less than n To embed a widget in your blog's sidebar, install the Wolfram|Alpha Widget Sidebar Plugin, and copy and paste the Widget ID below into the 'id' field: We appreciate your interest in Wolfram|Alpha and will be in touch soon. INTRODUCTION TO CRYPTOGRAPHY - (CS55N) (2015) - Dan Bonehs, Applied Crypto Group, Stanford Security Laboratory, Department of Computer Science, School of Engineering, Stanford University; Course Hosted by Coursera Multimedia Introduction to … A online ElGamal encryption/decryption tool. They wish to encrypt a message M so that both their keys are needed for decryption. There are 2 modes of operation - Triple ECB (Electronic Code Book) and Triple CBC (Cipher Block Chaining). Elgamal: Signature Algorithm Alice (Key generation): As before. Problem 2. Check Try example (P=23, G=11, x=6, M=10 and y=3) Try! With the spread of more unsecure computer networks in last few decades, a genuine need was felt to use cryptography at larger scale. Then a primitive root modulo p, say α, is chosen. It can be considered the asymmetric algorithm where the encryption and decryption happen by using public and private keys. Algorithm 1.3: Decryption for the CRT-ElGamal. The ElGamal public key consists of the three parameters (p, g, y). Smith and based on Lucas sequences. Keys are not eventually exchanged – they are joint and derived. is the same, as are the answers. The ElGamal Encryption Scheme is an asymmetric key encryption algorithm for public key cryptography algorithm for public key cryptography and it is based on Diffie Helman key exchange. Private Key. Find the corresponding secret key (N;d). For example, suppose that p = 17 and that g = 6 (It can be confirmed that 6 is a generator of group Z 17). Text to encrypt: Encrypt / Decrypt. Diffie-Hellman key exchange is a simple public key algorithm. So the sisters decide to communicate con dentially using a modi cation of the ElGamal cryptosystem, referred to as the Frozen ElGamal Cryptosystem. With a focus on public-key cryptography, the book describes RSA ciphers, the Diffie-Hellman key exchange, and ElGamal ciphers. The cryptosystem takes its name from its inventors R ivest, S hamir and A dleman. This cryptosystem is based on the difficulty of finding discrete logarithm in a cyclic group that is even if we know g a and g k, it is extremely difficult to compute g ak.. Asymmetric encryption is used by multiple users and across open networks, like the Internet, because the public key can be freely shared without risking data theft. Technically, the time estimate of your code is correct (that is, if you insert modulo operations when you update pow1 and pow2), however no one would actually use that algorithm to do ElGamal. ElGamal Cryptosystem is a public key cryptosystem and asymmetric cryptosystem. To demonstrate the calculator’s abilities. S A = x is Alice’ RSA private key. First need to calculate the key pair (private key and public key). Its security is based on the intractability of the discrete logarithm problem (DLP) and the Diffie-Hellman Problem (DHP) [3,4] Hellman key exchange . 1.1– El Gamal Algorithm Step 1 – Global Public Elements – As with Diffie-Hellman, to generate a ElGamal, Taher (1985). Jakobsson M (1998) A practical mix. This page contains one of the most extensive Web sites for encryption, and includes secret key, public key and hashing methods. During the 1970s, the astounding idea of public key cryptography burst upon the scene.1 In a public key cryptosystem, Alice has two keys, a public encryption key K Pub and a private (secret) decryption key … It is an approach used for public key encryption by utilizing the mathematics behind elliptic curves in order to generate security between key pairs. Public-Key cryptography was invented in the 1970s by Whitfield Diffie, Martin Hellman and Ralph Merkle. This semester we studied Paillier Cryptography. Key generation [edit | edit source] The key generator works as follows: Alice generates an efficient description of a multiplicative cyclic group of order with generator. In 1985, Tahar Elgamal (b. The RSA operation can't handle messages longer than the modulus size. ... ElGamal is a public-key cryptosystem developed by Taher Elgamal … • Can the attacker impersonate the bank? This function will only crack keys 40 bits long or shorter. LetGbe the groupZ∗p={1,2,...,p−1}under multiplication modulop. The ElGamal encryption system is a public key encryption algorithm by Taher Elgamal in 1985 that is based on the Diffie-Hellman key exchange. 2. We will adapt this equation into elliptic curves. Section 16.3 ElGamal Encryption System. G q. The following are the major asymmetric encryption algorithms used for encrypting or digitally signing data. I recognized from the signature files, that the given r-values are the same (r1 = r2 = r). Bob also selects his secret key X between 1 and p-1. The vital piece of The private key x can be any number bigger than 1 and smaller than 71, so we choose x = 5. What is ElGamal? Alice (sign message M and send to Bob): 1 Pick a random number k. 2 Compute the signature S = (a,b): a = gk mod p This method uses ideas about group theory and complexity issues for its security. This tool uses the mcrypt_encrypt() function in PHP, so for more infos about the parameters used check the manual. Alice begins by publishing information consisting of a public key and an algorithm. bc – an arbitrary precision calculator ... ElGamal Taher ElGamal, Netscape DSA NSA, NIST. You might also like the online decrypt tool.. Key:. ECC can be used for encryption (e.g Elgamal), secure key exchange (ECC Diffie-Hellman) and also for authentication and verification of digital signatures This is An ElGamal encryption key is constructed as follows. This cryptosystem is based on the difficulty of finding discrete logarithm in a cyclic group that is even if we know g a and g k, it is extremely difficult to compute g ak.. For example, suppose that p = 17 and that g = 6 (It can be confirmed that 6 is a generator of group Z 17 ). [m = c{_2} . s^{-1} mod p] which can be rewritten (dagger) as Try example (P=71, G=33, x=62, M=15 and y=31) Try! Alice has Bob's public key. Problem 1 { ElGamal Cryptosystem (10 points) Anna and Elsa are making plans for the summer, but they want to keep those plans hidden from Olaf the Snowman. (4 Pts Each) Alicechooses A Prime P And An Elliptic Curve E : Y2 23 + Ax + B Over Fp, As Well As A Point PE E(Fp) Of Large Order (if Possible). RSA Encryption Test. Recall the (randomised) Elgamal cryptosystem. As it is a Public key cryptography, it needs two different keys. To embed this widget in a post on your WordPress blog, copy and paste the shortcode below into the HTML source: To add a widget to a MediaWiki site, the wiki must have the. Nov. 29 Rundown of Applied Encryption 2 Python script: Elgamal Dec. 6 Final Projects Presentations Final Paper VI.Course Requirements • Python Scripts Python assignments will make up the majority of your homework. Up to this point, Alice and Bob can’t communicate securely with each other because they’ve yet to exchange public keys. In public key cryptosystems there are two keys, a public one used for encryption and and private one for decryption. This is a small application you can use to understand how Elgamal encryption works. The ElGamal signature scheme is a digital signature scheme based on the algebraic properties of modular exponentiation, together with the discrete logarithm problem. 2. The security of the ElGamal signature scheme is based (like DSA) on the discrete logarithm problem ().Given a cyclic group, a generator g, and an element h, it is hard to find an integer x such that g^x = h.. Generating the public key. On the processing speed front, Elgamal is quite slow, it is used mainly for key authentication protocols. $endgroup$ – Ilmari Karonen May 16 '17 at 18:38 The ElGamal Encryption Scheme is an asymmetric key encryption algorithm for public key cryptography algorithm for public key cryptography and it is based on Diffie Helman key exchange. There are several other variants. Step 6 : Public Key {e,n} Private Key {d,n} Step 7 : Cipher text C = P e mod n where P = plaintext. 4. c. Suppose an attacker obtains the private key for a central Certificate Authority. ElGamal and Chosen Ciphertext Attacks Recall that to use the ElGamal public key encryption scheme, Alice randomly selects a private key x 2Z p and computes her public key as y = gx mod p, where g is a publicly known generator of Z p. To encrypt a message m 2Z p for Alice, Bob randomly selects r 2Z p and computes the ciphertext as c = (g r;my ). 1 Pick a prime p. 2 Find a generator g for Z p. 3 Pick a random number x between 1 and p −2. There are three steps for this, Key GenerationEncryptionDecryption Here is the code for this cyrptosystem. Encrypting the whole message twice is too expensive!! What pair of integers in Z ∗ 41 does Banba send to Aoibh? PyCrypto before 2.6 does not produce appropriate prime numbers when using an ElGamal scheme to generate a key, which reduces the signature space or public key space and makes it easier for attackers to conduct brute force attacks to obtain the private key. encryption system is an asymmetric key encryption algorithm for public-key cryptography which is based on the Diffie–Hellman key exchange. The encryption key is the ordered triple (p,α,β). With a focus on public-key cryptography, the book describes RSA ciphers, the Diffie¿Hellman key exchange, and ElGamal ciphers. At the root is the generation of P which is a prime number and G (which is a value between 1 and P-1) [].. Blowfish, DES, TripleDES, Enigma). Alice has Bob's public key. Public key cryptography Asymmetric key systems can be used in public key cryptography Public Encryption Key Secret Decryption Key Anyone Bob Eve Encrypt Decrypt. Letpbe a prime. ElGamal Decryption Added Nov 22, 2015 by Guto in Computational Sciences Decrypt information that was encrypted with the ElGamal Cryptosystem given y, a, and p. Show that Alice and Bob output the same key. On the processing speed front, Elgamal is quite slow, it is used mainly for key authentication protocols. GitHub. The group is the largest multiplicative sub-group of the integers modulo p, with p prime. Setting up the ElGamal public key cryptosystem • Alice selects a primitive element g in Z p* . 1024-bit RSA modulus vs. 128-bit AES keys). Key generation. The ElGamal key pair consists of a private key s and the corresponding public key h=g s mod p. The private key s is a randomly chosen integer such that 0