- Autel maxidas ds708 Auto Diagnosis auto diagnostic tool BMW Diagnostic tool bmw enet cable BMW ENET Interface Cable BMW ICOM BMW ICOM A2 bmw scanner condor mini Easycoding Ford VCM 2 Foxwell FVDI 2018 GM MDI Gm Tech 2 GM Tech2 Honda HDS ICOM A2 ICOM A2+B+C ikeycutter condor jlr mangoose Lexia 3 MB SD C4 mb sd compact c4 MB SD Connect C4 MB SD.
- Click Settings again and then click Activation Parameters. Enter your name and email address and click Save Activation Parameters Optional. If you would like your workshop name, address, telephone number or other details included on any printouts or reports you save in VAUX-COM enter them on the left under Workshop Details.
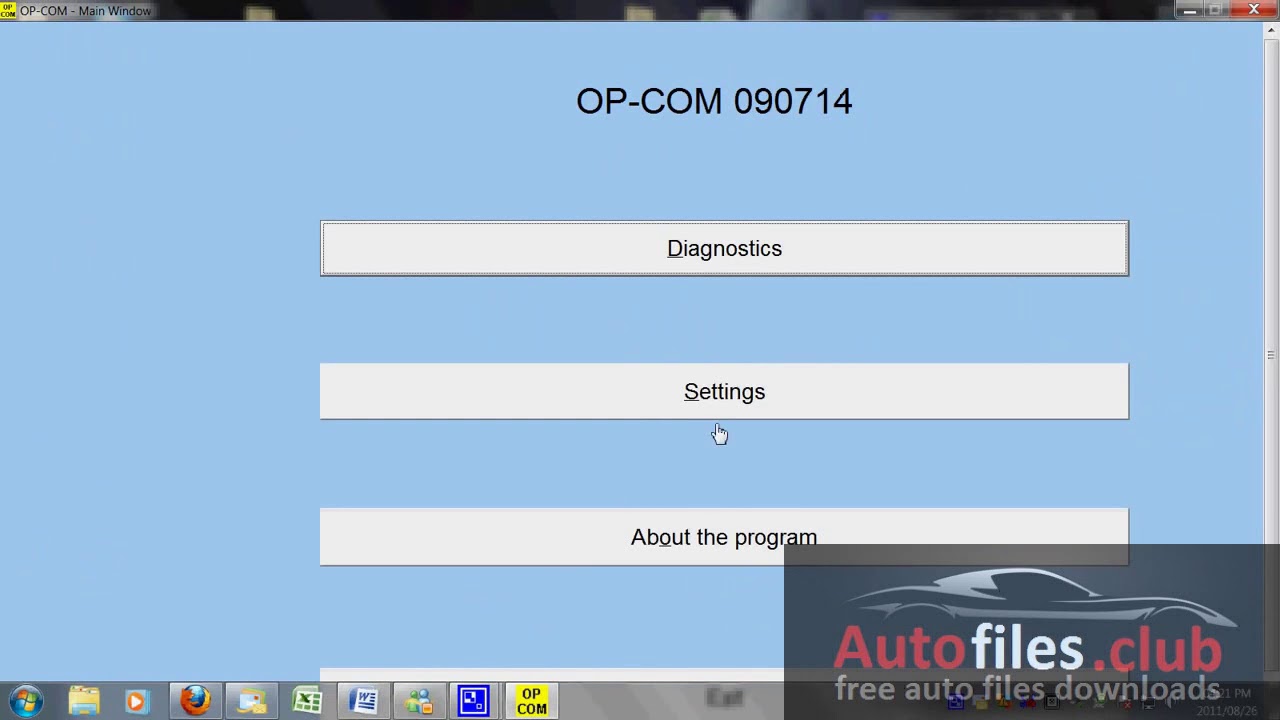
- Instruction how to Install and Activate OPCOM Opel diagnostic software.
- Opcom Activate Password Execution Button
- Opcom Activate Password Execution Tool
- Opcom Activate Password Execution Download
- Opcom Activate Password Execution Software
Once enrolled, you must sign in and complete your security questions. Upon sign in, you'll be able to see the current and available balances for all your checking, savings, money market, credit card, HELOC, installment loan, mortgage, CD, and IRA accounts. You'll start to see transactions (checks cleared, deposits, etc.) on the next business day. We would like to show you a description here but the site won’t allow us.
The customize operation (-C flag) can be executed at this time. The running system's operating system must be a version greater than or equal to the operating system version of the volume group that undergoes the 'wake-up.' This might mean that it is necessary to boot from the altinst_rootvg and 'wake up' the old_rootvg. Op-com Help Needed - posted in VX220 Discussion: I have just bought a Op-com off flee bay trouble is i can't get it to work keeps asking for activation code which i cant find i tried registering it but it says chines illegal copy i have emailed the seller but know reply just wondered if anyone has any ideas. I tested it also and it can program Underhood electrical center UEC which 090820d couldn't work, i used it on vectra C for daytime running lights adjustment (mode 3) Hvala VZ. I've read the 'opcom activation.pdf' and i didn't find the 'activate password.exe' file from the second point. Where i can find it?
 -->
-->This article describes the password policies and complexity requirements associated with user accounts in your Azure Active Directory (Azure AD) tenant.
Administrator reset policy differences

Microsoft enforces a strong default two-gate password reset policy for any Azure administrator role this policy may be different from the one you have defined for your users and cannot be changed. You should always test password reset functionality as a user without any Azure administrator roles assigned.
With a two-gate policy, administrators don't have the ability to use security questions.
The two-gate policy requires two pieces of authentication data, such as an email address, authenticator app, or a phone number. A two-gate policy applies in the following circumstances:
All the following Azure administrator roles are affected:
- Helpdesk administrator
- Service support administrator
- Billing administrator
- Partner Tier1 Support
- Partner Tier2 Support
- Exchange administrator
- Skype for Business administrator
- User administrator
- Directory writers
- Global administrator or company administrator
- SharePoint administrator
- Compliance administrator
- Application administrator
- Security administrator
- Privileged role administrator
- Intune administrator
- Application proxy service administrator
- Dynamics 365 administrator
- Power BI service administrator
- Authentication administrator
- Privileged Authentication administrator
If 30 days have elapsed in a trial subscription; or
A vanity domain is present, such as contoso.com; or
Azure AD Connect is synchronizing identities from your on-premises directory
Exceptions
A one-gate policy requires one piece of authentication data, such as an email address or phone number. A one-gate policy applies in the following circumstances:
- It's within the first 30 days of a trial subscription; or
- A vanity domain isn't present (*.onmicrosoft.com); and
- Azure AD Connect isn't synchronizing identities
UserPrincipalName policies that apply to all user accounts
Every user account that needs to sign in to Azure AD must have a unique user principal name (UPN) attribute value associated with their account. The following table outlines the policies that apply to both on-premises Active Directory user accounts that are synchronized to the cloud and to cloud-only user accounts:
| Property | UserPrincipalName requirements |
|---|---|
| Characters allowed |
|
| Characters not allowed |
|
| Length constraints |
|
Password policies that only apply to cloud user accounts
The following table describes the password policy settings applied to user accounts that are created and managed in Azure AD:
| Property | Requirements |
|---|---|
| Characters allowed |
|
| Characters not allowed |
|
| Password restrictions |
|
| Password expiry duration |
|
| Password expiry notification |
|
| Password expiry |
|
| Password change history | The last password can't be used again when the user changes a password. |
| Password reset history | The last password can be used again when the user resets a forgotten password. |
| Account lockout | After 10 unsuccessful sign-in attempts with the wrong password, the user is locked out for one minute. Further incorrect sign-in attempts lock out the user for increasing durations of time. Smart lockout tracks the last three bad password hashes to avoid incrementing the lockout counter for the same password. If someone enters the same bad password multiple times, this behavior will not cause the account to lockout. |
Set password expiration policies in Azure AD
A global administrator or user administrator for a Microsoft cloud service can use the Microsoft Azure AD Module for Windows PowerShell to set user passwords not to expire. You can also use Windows PowerShell cmdlets to remove the never-expires configuration or to see which user passwords are set to never expire.
This guidance applies to other providers, such as Intune and Office 365, which also rely on Azure AD for identity and directory services. Password expiration is the only part of the policy that can be changed.
Note
Only passwords for user accounts that are not synchronized through directory synchronization can be configured to not expire. For more information about directory synchronization, see Connect AD with Azure AD.
Set or check the password policies by using PowerShell
Opcom Activate Password Execution Button
To get started, you need to download and install the Azure AD PowerShell module. After you have it installed, you can use the following steps to configure each field.
Check the expiration policy for a password
Connect to Windows PowerShell by using your user administrator or company administrator credentials.
Execute one of the following commands:
- To see if a single user’s password is set to never expire, run the following cmdlet by using the UPN (for example, aprilr@contoso.onmicrosoft.com) or the user ID of the user you want to check:
- To see the Password never expires setting for all users, run the following cmdlet:
Set a password to expire
Connect to Windows PowerShell by using your user administrator or company administrator credentials.
Execute one of the following commands:
- To set the password of one user so that the password expires, run the following cmdlet by using the UPN or the user ID of the user:
- To set the passwords of all users in the organization so that they expire, use the following cmdlet:
Set a password to never expire
Connect to Windows PowerShell by using your user administrator or company administrator credentials.
Execute one of the following commands:
- To set the password of one user to never expire, run the following cmdlet by using the UPN or the user ID of the user:
- To set the passwords of all the users in an organization to never expire, run the following cmdlet:
Warning
Passwords set to
-PasswordPolicies DisablePasswordExpirationstill age based on thepwdLastSetattribute. If you set the user passwords to never expire and then 90+ days go by, the passwords expire. Based on thepwdLastSetattribute, if you change the expiration to-PasswordPolicies None, all passwords that have apwdLastSetolder than 90 days require the user to change them the next time they sign in. This change can affect a large number of users.
Next steps
The following articles provide additional information about password reset through Azure AD:
- Reset or change your password.
- Register for self-service password reset.
Join GitHub today
GitHub is home to over 40 million developers working together to host and review code, manage projects, and build software together.
Sign upHave a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Comments
Environment data
Actual behaviorCreate python terminal results in a powershell error Expected behaviorI don't need need to disable running scripts in able to use VS code Steps to reproduce:
|
commented Sep 12, 2018
Hmmm. this feels like it might be a VSCode problem. To fix the issue, you can simply open a Powershell window as administrator and type the following: And hit enter, respond |
I take it back - we are running an activate.ps1 file from a .venv! Hmmm.. not sure what we can do about this from the extension's perspective. @DonJayamanne can we inject some powershell code prior to running |
added type-bugneeds PRfeature-terminal labels Sep 12, 2018
added type-enhancement and removed type-bug labels Sep 12, 2018
Yes we can. @d3r3kk |
changed the titleactivate.ps1 fails because running scripts is disabled by default on WindowsSep 12, 2018
Yep, that's pretty standard Powershell behaviour/expected workflow on a new machine. Not sure we should usurp that is what I'm getting at. However, if we choose to do so, it shouldn't be too difficult to put a quick popup and ask the user if doing so will be ok with them first (much like the powershell cmdlet |
commented Sep 12, 2018
Agreed. @qubitron thoughts |
Why do we even need powershell cmdlet to do this, why can't we run a batch file or something else that doesn't require admin privileges/execution policies to be set? |
commented Sep 12, 2018
It's a PowerShell script because that's how you get the prompt updated to list the virtual environment's name: https://github.com/python/cpython/blob/master/Lib/venv/scripts/nt/Activate.ps1 |
The other option any notification could have is offer to switch off the automatic activation on top of providing instructions on how to change the policy. |
commented Sep 12, 2018
OK, so really this is an issue because we're using a powershell cmd prompt instead of CMD (which is what I use outside of VS Code and just lets me activate without having to set any policies). Since I assume we can't change the default from powershell to cmd, detecting the issue and prompting users to set the execution policy (with a button) seems like the right solution. |
commented Sep 13, 2018 •
Well, we could do the following:
I.e. where possible use batch files. |
commented Oct 26, 2018
It might also be easier for us to contribute upstream to Python an |
Opcom Activate Password Execution Date
Just to add to the description of the issue at hand I had same problem using Pipenv virtual environment. Pipenv version: 2018.11.14 Worked after updating my execution policy from using the following PS cmdlet: Here is the link to the documentation on ExecutionPolicy from Microsoft Cheers |
Not sure if this happens after the latest update but when I execute 'Run current file in terminal', it tries to activate the environment that resides in the same directory with the script itself, it fails and afterwards it executes the script with the python interpreter that is inside my environment. How come ? |
commented Feb 8, 2019
@BurakcanK Is the problem due to Powershell permissions not being set? If so, please run (as admin on your system) the If that is not the problem you are seeing, please feel free to open another issue with the specific details of your situation. |
commented Mar 31, 2019
I was able to work around this problem by adding the following to my VS Code settings: |
OPEN POWERSHELL IN ADMINISTRATER MODE AND USE THIS COMMANDS I hope your problem is solved |
commented Jul 3, 2019
If https://bugs.python.org/issue37354 can be solved then |
This Work on my windows 10 |
commented Aug 9, 2019
Watch python/cpython#14967, may even make it into 3.8. |
@d3r3kk it won't make it into 3.8. |
commented Aug 9, 2019
@luabud@brettcannon we should evaluate other solutions since this won't be fixed within the next 1-2 years on the Python side then. At a minimum, let's make sure to include this step in our getting started docs. |
@qubitron docs are probably going to be all we can do for this as I'm not comfortable overwriting someone's |
Opcom Activate Password Execution Tool
commented Aug 9, 2019 • edited
edited
@qubitron@brettcannon Agreed on the docs part, but what about prompting to change the execution policy for PowerShell in VS Code, and if 'yes' is selected then we add 'terminal.integrated.shellArgs.windows': ['-ExecutionPolicy', 'Bypass'] to settings.json? |
@luabud we could, but I'm a little hesitant since it's a security change so we would have to be very careful and clear on the messaging of what they are opting into having us do on their behalf. |
commented Aug 10, 2019
@qubitron@brettcannon looks like we already have that on our Getting Started tutorial: https://code.visualstudio.com/docs/python/python-tutorial#_install-and-use-packages |
It's pretty buried in there, I think it should be higher up as a pre-requisite, and the doc it links to lists a ton of options, when it could be more prescriptive and say: Open an administrator powershell prompt (windows key -> type 'Powershell' -> Ctrl+Shift+Enter), and then type: |
commented Aug 12, 2019
I think maybe? |
Bit shocked Steve's taking that as a bugfix, but |
commented Aug 13, 2019 • edited
edited
Not sure whether we've explored this.
Pros:
Finally: I tried and works on a vanilla Windows 10 setup (had to install one today to test something else).
|
commented Aug 13, 2019 •
Unless no one has any objections, I'd like to revisit this, at least as a spike. |
added this to the 2019 - August Sprint 16 milestone Aug 13, 2019
|
After installation or major reinstall update, you'll need to activate VAUX-COM before you can use it on a car.
NOTE: Your license allows you to run VAUX-COM on as many computers as you wish.
First click [Settings]
Now select your interface revision type from the drop down list and click [Save Config] (screen will close)
TIP: If you do not know your interface revision type, check the label or see VAUX-COM - Settings - Interface Revision Type
Opcom Activate Password Execution Tool
Click [Settings] again and then click [Activation Parameters]. Enter your name and email address and click [Save Activation Parameters]
Optional. If you would like your workshop name, address, telephone number or other details included on any printouts or reports you save in VAUX-COM enter them on the left under Workshop Details. You can leave this blank if you prefer
Opcom Activate Password Execution Download
Here is an example Fault Code Saved file with the workshop details as shown above
To activate automatically online, connect your interface to the USB port on your computer and wait a few seconds for the driver to install, then click [Diagnostics]
Opcom Activate Password Execution Software
After a few seconds the activation will be complete (if the machine you are running VAUX-COM on does not have an Internet connection, please contact us for instructions on manually activating the software)